Why do an intrusion test on its WordPress site in 2025

Why a Penetration Test is MANDATORY for Your Wordpress Site in 2025 ?
Introduction
WordPress, as one of the most widely used content management systems (CMS) in the world, powers a significant portion of websites, ranging from personal blogs to corporate sites.
However, its popularity comes with increased security risks, making penetration testing crucial for safeguarding these sites against cyber attacks.
📈 Some staggering statistics (according to lesmakers.fr):
- The #1 CMS in the world.
- Over 62% market share among CMS.
- More than 43% of global websites use WordPress.
- 9,000 free themes.
- 60,000 free active plugins.

More than 62% of sites using a CMS opt for WordPress

Over 455 million websites worldwide use WordPress.
A double-edged sword of popularity
WordPress is often targeted by attackers due to its widespread use.
Vulnerabilities in WordPress core, themes, or plugins can be exploited to compromise a site. Penetration testing helps identify these weaknesses before they can be exploited by malicious actors.
More alarming statistics 😅
- In 2023, there were over 90 million attacks against WordPress sites. (source: https://www.wordfence.com/)
- More than 50% of WordPress sites are attacked each year. (source: https://sucuri.net/)
- Over 90% of attacks on WordPress sites target vulnerabilities in plugins, themes, or WordPress core itself. (https://www.wordfence.com/)
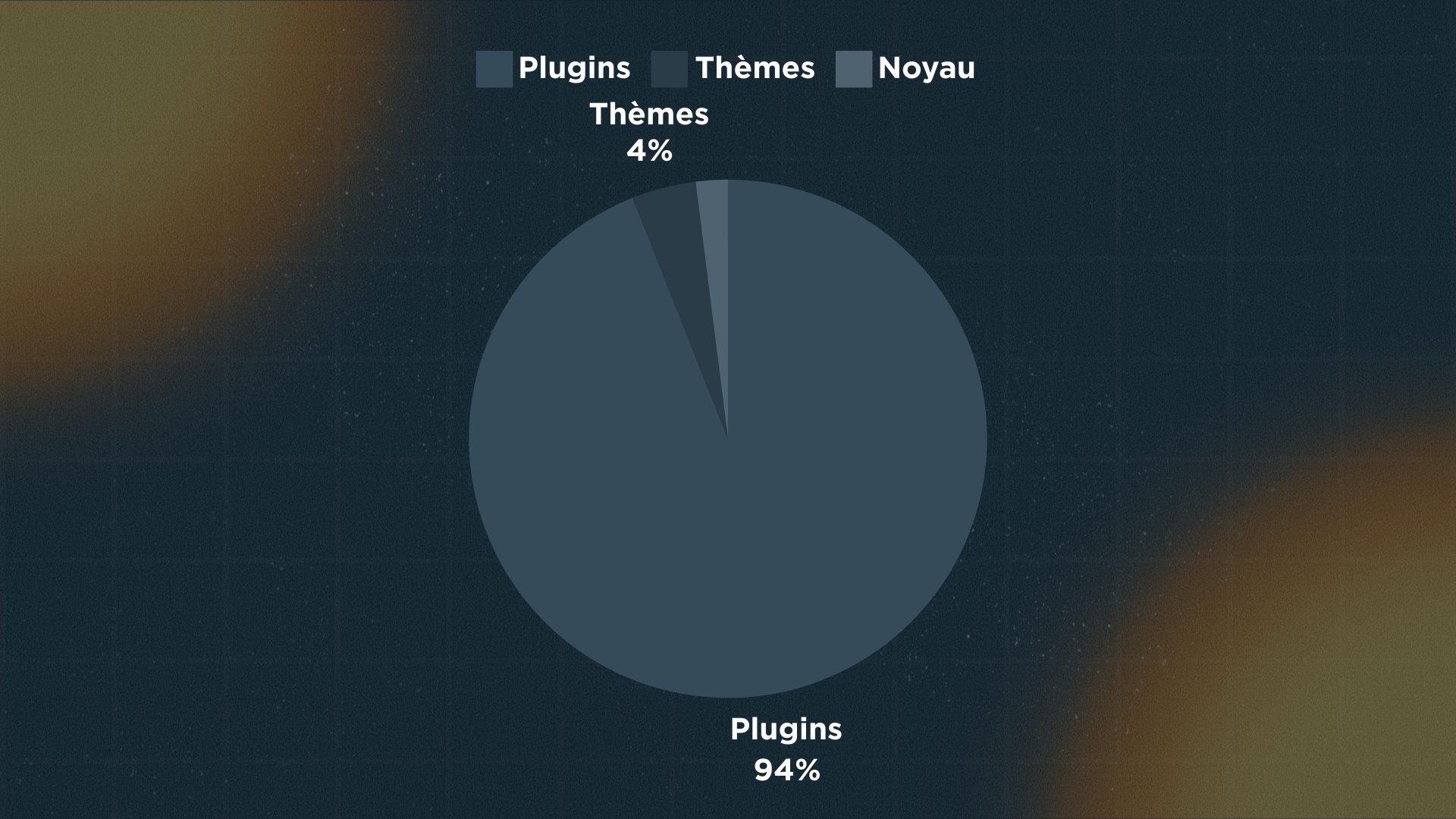
Proportion of CMS WordPress vulnerabilities (source: wpscan.com).
Why protect yourself?
Might seem like an obvious question, right? 😉
For several reasons:
- To protect sensitive data: WordPress sites often host sensitive data, such as user personal information and payment details.
- To comply with security standards: For businesses, compliance with security standards like GDPR or PCI DSS is not an option but a requirement.
- To improve reputation and trust: A secure site enhances user and customer trust. Conversely, a compromised site can severely damage a company’s reputation.
- To prevent financial losses: Cyber attacks can lead to significant financial losses due to data theft, ransom for decrypting data, or the costs of restoring services.
- To ensure business continuity: A successful cyber attack can disrupt a WordPress site’s operations, leading to downtime and affecting business continuity.
Penetration testing: protection through attack

A penetration test, also known as a pentest, is an effective way to simulate an attack and identify security flaws in your WordPress site.
Addressing the challenges
Let’s revisit the previous challenges and apply them to the realm of penetration testing:
- Protecting sensitive data: A penetration test helps assess the robustness of data protection mechanisms, ensuring their integrity and confidentiality.
- Complying with security standards: A penetration test reveals whether a WordPress site meets requirements, thus avoiding potential penalties related to non-compliance.
- Improving reputation and trust: Penetration tests help preserve reputation by ensuring site security.
- Preventing financial losses: Penetration tests help prevent incidents by detecting vulnerabilities that could be exploited.
- Identifying weaknesses in custom configurations: Many WordPress sites are heavily customized, with bespoke themes and specific plugins. These customizations can introduce unique security flaws that only a penetration test can effectively identify and evaluate.
- Ensuring business continuity: Penetration tests help maintain site availability and reliability, essential for online business activities.
Methodology
At Trackflaw, we are equipped to conduct a comprehensive audit of your WordPress site to eliminate all risks (lucky you)! 😉
This methodology revolves around major steps, beginning with a reconnaissance phase.
Reconnaissance
The auditor starts by collecting basic information:
- Determine the WordPress version, plugins, and themes used.
- Identify the technologies and frameworks used (
JavaScript,PHP, etc.). - Analyze
HTTPheaders for possible sensitive information.
For example, to verify if a website runs on WordPress:
| |
For example, to check if a website is running on WordPress:
Or else, you can also use the excellent Wappalyzer extension as shown in the screenshot below (the WordPress in the capture is not very secure, by the way…)! 😀

Subsequently, the pentester may attempt to retrieve files:
- Try to download potentially sensitive files, for example, those freely accessible in the
wp-contentsdirectory. - Look for backup files or unprotected configuration files.
A small example to obtain the list of plugins and themes (when possible)
Plugins
| |
Thèmes
| |
Finally, the auditor enumerates users:
- Identify existing users and roles on the site.
- Attempt to guess usernames and passwords through brute force or dictionary attacks.
Several methods to perform this action:
- By brute-forcing credentials:
curl -s -I -X GET http://vuln.trackflaw.com/?author=1. - Via the
wp-jsonroute:curl http://vuln.trackflaw.com/wp-json/wp/v2/users. - Through enumeration on the
wp-login.phppage.
Exploitation
Subsequently, the auditor is tasked with studying vulnerabilities impacting the site, its plugins, and its themes.
Some examples of vulnerabilities:
- SQL Injection Tests: Exploit security flaws in plugins or themes to inject malicious SQL code.
- Cross-Site Scripting (XSS): Inject malicious
JavaScriptcode into the site to redirect users. - Cross-Site Request Forgery (CSRF): Force an authenticated user to perform unwanted actions.
For this part, we leave it as an exercise to the reader. We can’t reveal all our secrets! 😉
Tooling
There are tools available that automate exploitation and ease the pentester’s task during penetration testing, such as:
CmsmapWpscan
Some examples below 👇
| |
Protecting yourself after the penetration test

Once you have performed your penetration test, it is important to follow certain steps to secure your website:
- Enable automatic updates with the code below:
| |
- Install security plugins like Wordfence, Sucuri Security, or iThemes Security.
Some other recommendations:
- Remove the default admin user.
- Use strong passwords with 2FA.
- Periodically review user permissions.
- Limit login attempts to prevent brute-force attacks.
- Rename
wp-admin.phpand restrict access to it internally or from certain IP addresses. - Disable directory listing.
Conclusion
Conducting a penetration test on your WordPress site is not a luxury but a necessity in the current digital environment. By proactively identifying vulnerabilities and enhancing site security, you can protect your digital assets, maintain user trust, and ensure the continuity of your business operations.
In the face of the growing threat of cyberattacks, penetration tests are an essential investment in the security of a WordPress site. Contact Trackflaw now!
 TRACKFLAW
TRACKFLAW